LPIC-102
Jump to navigation
Jump to search
LPIC-102
What does Linux mean?⌘

Outline⌘
- First Day:
- Session I:
- Introduction to the course
- Session II:
- Topic 105: Shells, Scripting and Data Management
- Session III:
- Topic 106: User Interfaces and Desktops
- Session IV:
- Topic 107: Administrative Tasks
- Session I:
Outline #2⌘
- Second Day:
- Session I:
- Topic 108: Essential System Services
- Session II:
- Topic 109: Networking Fundamentals
- Session III:
- Topic 110: Security
- Session IV:
- Case Study, Certification and Surveys
- Session I:
First Day - Session I⌘

LPI certification path⌘
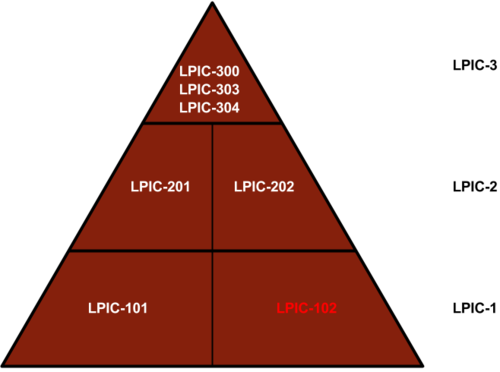
LPIC-101 exam⌘
- Detailed Objectives: https://www.lpi.org/linux-certifications/programs/lpic-1/exam-101/
- Certification Authorities:
- PearsonVUE: http://www.pearsonvue.com/
- Prometric: https://www.prometric.com/en-us/Pages/home.aspx
- Exam Cost: 173$ (prizes in local currency updated on a daily basis)
- Exam Duration: 90m base time + 30m additional time for piloting questions
- Exam Passing Score: 500 in 200 - 800 scale
- Certificate Expiration Date: 5 years
- Question Type: closed
- Exam Topic Weigths
Introduction to the lab⌘
Lab components:
- Laptop with Windows
- Virtual Machines with Linux on:
- VMs: Debian, CentOS
- Credentials:
- admin user: root / terminal
- non-admin user: terminal / terminal
- VirtualBox:
- 64-bit version (click here to download)
- Snapshots (top right corner)
- Press right "Control" key to release
First Day - Session II⌘

105.1 Customize and use the shell
environment⌘
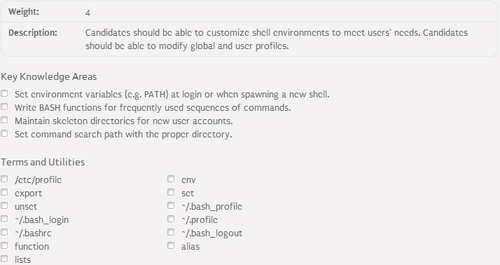
Environmental Variables⌘
- Environmental variable - variable defining a behavior of the environment
- Management tools:
- env - displays set environmental variables
- export - causes the environmental variable to be inherited by child processes
- set - sets a value of the environmental variable
- unset - unsets a value of the environmental variable
- The most common environmental variables:
- HOSTNAME - system hostname
- USERNAME - username
- PATH - paths in which to search executables
- PWD - current working directory
- LANG - locale category
Bash configuration files⌘
- Common bash configuration files:
| Type of File | Login File Location | Non-Login File Location |
|---|---|---|
| Global | /etc/profile and files in /etc/profile.d directory | /etc/bashrc or /etc/bash.bashrc |
| User | ~/.bash_login, ~/.profile or ~/.bash_profile | ~/.bashrc |
- Additional bash configuration files and directories:
- /etc/skel - skeleton directory for new user accounts
- ~/.bash_logout - user logout script
- ~/.inputrc - keyboard shortcuts configuration
Other bash customization tools⌘
- Aliases:
- defined by an alias built-in:
alias [alias]="[command]"
- Functions:
- defined by a function keyword
function [name] {
...
}
- Lists:
list=(item1 item2)
list[2]=item3
echo ${list[0]} ${list[1]} ${list[2]}
- Lab Exercise 105.1
105.2 Customize or write simple scripts⌘
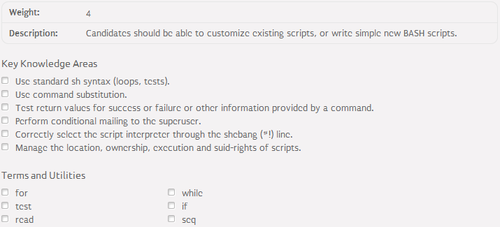
Bash scripting foudations⌘
- Execution permissions
- #! (shebang) - defines a path to the interpreter
- The most common Linux interpreters:
- /bin/bash (Bourne Again SHell)
- /bin/sh - standard shell
- /bin/tcsh (The C Shell)
- /usr/bin/expect
- /usr/bin/perl
- /usr/bin/python
IO Operations⌘
- Input operation:
read [variable]
- Output operation:
echo [output]
- Reading from file:
cat [file]
- Writing to file:
[command] > [file]
Conditional expressions⌘
- test:
test [expression] && [true command] || [false command]
- if:
if [ [expression] ]
then
[true command]
else
[false command]
fi
- case:
case [word] in
[pattern 1]) [command 1] ;;
[pattern 2]) [command 2] ;;
...
*) [command n] ;;
esac
Loops⌘
- for:
for [variable] in [list]
do
[command]
done
- seq:
seq [start] [stop]
- while:
while [ [condition] ]
do
[command]
done
- Lab Exercise 105.2
105.3 SQL data management⌘
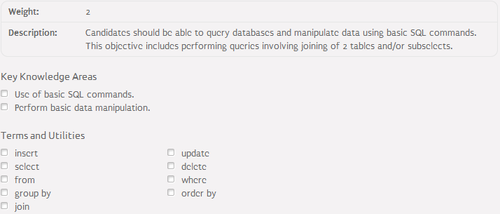
SQL and RDBMS⌘
- RDBMS (Relational DataBase Management system):
- database management system that is based on relational model
- the most popular Linux open-source RDBMS:
- MySQL - http://www.mysql.com/
- PostgreSQL - http://www.postgresql.org/
- SQLite - http://www.sqlite.org/
- SQL (Sequential Query Language):
- programming language designed for managing data held in a RDBMS
- SQL is an interpreted language
- de facto standard for managing structured data
Basic SQL commands⌘
- SELECT - retrieves data from one or more tables
- FROM - specifies the table(s) from which data is to be retrieved
- WHERE - includes a comparison predicate, which restricts the rows returned by the query
- GROUP BY - used to project rows having common values into a smaller set of rows
- ORDER BY - identifies which columns are used to sort the resulting data
- JOIN - used to join query results from two tables into one table
- INSERT - adds data to a table in a form of row
- INTO - specifies the table into which data is to be insterted
- VALUES - specifies the data to be insterted
- UPDATE - modifies a set of existing table rows
- SET - specifies the data to be modified
- DELETE - removes existing rows from a table
- Lab Exercise 105.3
First Day - Session III⌘

106.1 Install and configure X11⌘
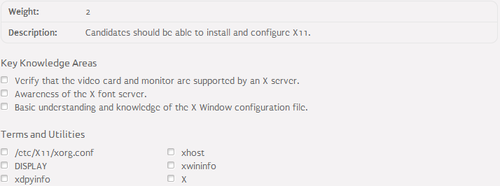
What is X11?⌘
- X11 - The X Window System - http://www.x.org/wiki/
- Windowing system for bitmap displays
- The most common GUI for UNIX-like operating systems
- Responsibilities:
- interacting with mouse and keyboard as an input device
- interacting with displays as an output device
- X11 does not mandate user interface!
- Principles of operations:
- client / server architecture
- network awareness
- x window manager
- List of supported video cards: http://www.x.org/wiki/Projects/Drivers/
History of X11⌘
- 1973 - first bitmap diplay system by Xeros (Alto)
- 1983 - initial idea of the X Window System
- 1985 - first release of the UWM (Ultrix Window Manager)
- 1987 - first release of the X11 system
- 1988 - first release of the XDM (X Display Manager)
- 1991 - fork between the MIT X Consortium and the XFree86 Project, Inc.
- 1993 - the MIT X Consortium transitions into the X Consortium, Inc.
- 1997 - the X Consortium, Inc. transitions into The Open Group
History of X11 #2⌘
- 1998 - first release of the KDE (K Desktop Environment) desktop
- 1999 - first release of the Gnome desktop
- 2004 - establishment of the X.Org Foundation
- 2004 - fork between the X.Org Foundation and the XFree86 Project, Inc.
- 2008 - last release of the XFree86 server
- 2009 - last commit into the XFree86 project
- 2014 - latest release of the X.Org Server
Desktops⌘
- X Window Manager + Additional Software = Desktop
- The most popular Linux desktops:
- GNOME - http://www.gnome.org/
- KDE - http://www.kde.org/
- Unity - https://unity.ubuntu.com/
- Cinnamon - http://cinnamon.linuxmint.com/
- XFCE - http://www.xfce.org/
- Android Desktop / ChromeOS
- The most common Linux distribution releases:
- server - no X11 and no desktop
- desktop - X11 and desktop
X11 installation⌘
- Standard installation:
cd /usr/src wget http://xorg.freedesktop.org/releases/individual/xserver/xorg-server-1.15.99.903.tar.gz tar -xzf xorg-server-1.15.99.903.tar.gz cd xorg-server-1.15.99.903 ./configure make make install
- Package-based installation:
- CentOS:
yum groupinstall "X Window System"
- Debian:
apt-get install x-window-system
- Some distributions support installation of both X11 and default desktop in one:
- Ubuntu:
apt-get install ubuntu-desktop
X11 configuration⌘
- /etc/X11/xorg.conf - main X11 configuration file:
Section [SectionName]
[SectionEntry]
...
EndSection
man xorg.conf
- Section entries:
- InputDevice - keyboard and mouse
- Monitor - monitor
- Device - video card
- Screen - monitor and video card combination
- Display - video mode
- Files - font server
- Automatic X11 configuration (X Server must be stopped):
X -configure mv /root/xorg.conf /etc/X11/xorg.conf
X11 management⌘
- Management tools:
- startx - starts the X Server
- xdpyinfo - displays information about the X Server
- xwininfo - displays information about windows
- xhost - access control program for the X Server
- DISPLAY environmental variable:
- [hostname]:[display].[screen]
- example: localhost:0.1
- Lab Exercise 106.1
106.2 Setup a display manager⌘
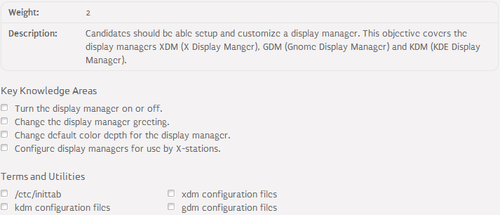
Display manager⌘
- Program that allows starting of a session on an X server
- The most popular Linux display managers:
- GDM (Gnome Display Manager) - https://wiki.gnome.org/Projects/GDM
- KDM (KDE Display Manager) - https://wiki.archlinux.org/index.php/KDM
- XDM - http://www.pl.freebsd.org/doc/handbook/x-xdm.html
- LightDM - https://wiki.archlinux.org/index.php/LightDM
Logging into the system⌘
- Logging into the system without display manager:
- CLI logon
- startx
- Logging into the system with display manager:
- GUI logon
- Runlevels with graphical modes:
- 2 on Debian
- 5 on RedHat
- Changing runlevels:
- telinit - temporarily
- /etc/inittab - permanently
Configuration⌘
- GDM:
- /etc/X11/gdm/gdm.conf - main configuration file
- key=value pairs grouped by sections
- KDM:
- /etc/X11/kdm/kdmrc - main configuration directory
- key=value pairs grouped by sections
- XDM:
- /etc/X11/xdm/xdm-config - main configuration file
- key: value pairs grouped by sections
- LightDM:
- /etc/lightdm/lightdm.conf - main configuration file
- key=value pairs grouped by sections
Remote access⌘
- With X11:
- Direct Connection
- XDMCP (X Display Manager Control Protocol) - http://en.tldp.org/HOWTO/XDMCP-HOWTO/
- X Forwarding using SSH - http://en.tldp.org/HOWTO/XDMCP-HOWTO/ssh.html
- Without X11:
- VNC (Virtual Network Computing) - https://www.realvnc.com/
- RDP (Remote Desktop Protocol) - http://msdn.microsoft.com/en-us/library/aa383015(v=vs.85).aspx
- Lab Exercise 106.2
106.3 Accessibility⌘
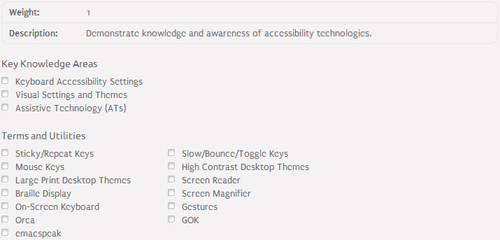
Keyboard and mouse accessibility settings⌘
- Keyboard repeat time - repeat rate and delay of the keyboard
- Sticky keys - causes keyboard modifier keys (Ctrl, Alt and Shift) to "stick" when pressed
- Slow keys - requires a key to be pressed for longer than a specified period of time
- Bounce/debounce keys - treats multiple press of a key as a single press
- Mouse tracking and click options - adjusts mouse tracking and click options
- Simulated mouse clicks - simulates mouse click / double click
- Mouse emulation/mouse navigation - enables mouse emulation by cursor keypad
- Mouse gestures - keyboard shortcuts for mouse
- Online keyboard - keyboard emulator
Screen accessibility settings⌘
- Fonts - adjust fonts used by the system
- Contrast - adjust display contrast
- Magnifier - enlarges part of the screen
Assistive technologies⌘
- Screen Reader - assists blind people in terms of reading:
- Audio Desktop - assists blind people in terms of writing:
- Emacspeak - http://emacspeak.sourceforge.net/
- Baille Display - display for blind people
- BRLTTY - http://mielke.cc/brltty/
- Lab Exercise 106.3
First Day - Session IV⌘

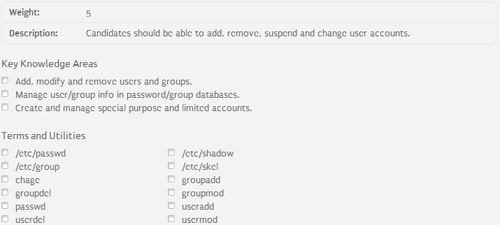
User and group accounts management⌘
- Configuration files:
- /etc/passwd - user database
- /etc/shadow - user password database
- /etc/group - group database
- /etc/gshadow - group password database
- Management tools:
- groupadd - creates a group
- groupdel - deletes a group
- groupmod - modifies a group
- passwd - modifies user password
- useradd - creates a user
- userdel - deletes a user
- usermod - modifies a user
/etc/passwd file⌘
- Structure:
[username]:[password information]:[UID]:[GID]:[GECOS]:[home directory]:[program]
- username - user name / login
- password information:
- empty - no password
- x - password hash in /etc/shadow file
- * - account locked
- ! - account locked
- UID (User IDentifier) - user number
- GID (Group IDentifier) - user group number
- GECOS (General Electric Comprehensive Operating System) - user full name and contact information
- home directory - a path to user home directory
- program - a program which is started when the user logs into the system (e.g. shell)
/etc/shadow file⌘
- Structure:
[username]:[hash]:[change date]:[min age]:[max age]:[warn period]:[grace period]:[exp date]:[reserved]
- username - user name / login
- hash - user password hash
- change date - last password change date:
- counted in days starting from the 1st of January 1970
- 0 - user will be asked to change its password during the next login
- empty - date checking disabled
- min age - minimum number of days after which the password can be changed
- max age - maximum number of days after which the password can be changed
- warn period - how many days before password expiration date is the user warned
- grace period - how many days after password expiration date can the user log in
- exp date - account expiration date counted in days starting from the 1st of January 1970
- reserved - reserved for future use
/etc/group file⌘
- Structure:
[group name]:[password information]:[GID]:[members]
- group name - group name
- password information:
- empty - no password
- x - password hash in /etc/gshadow file
- * - account locked
- ! - account locked
- GID - group number
- members - comma-separated list of users
- Lab Exercise 107.1
107.2 Automate system administration tasks
by scheduling jobs⌘
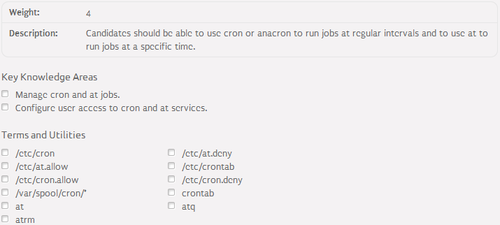
Scheduling jobs in Linux⌘
- Jobs run on regular basis:
- on computers running continuously:
- cron daemon
- on computers not running continuously:
- anacron utility
- on computers running continuously:
- Jobs run once:
- at command
Scheduling jobs to be run on regular basis
on computers running continuously⌘
- Configuration files:
- /etc/cron.allow - contains new-line separated list of users allowed to access cron service
- /etc/cron.deny - contains new-line separated list of users denied to access cron service
- /var/spool/cron/* - physical location of crontab files
- Management tools:
- crontab - crontab management utility
- crond - cron daemon binary
Crontab⌘
- Structure:
[minute] [hour] [DoM] [month] [DoW] [username] [command]
- minute - job is executed specified number of minutes after a full hour
- hour - job is executed at specified hour
- DoM - job is executed on specified day of the month
- month - job is executed in specified month
- DoW - job is executed on specified day of the week
- command - command to be executed by cron
- Crontab tricks:
- 1-n - 1, 2, ... , n
- */m - 0, m, 2m, ...
- 0-n/m - 0, m, 2m, ... , n
- x,y,z - x, y, z
Scheduling jobs to be run on regular basis
on computers not running continuously⌘
- Anacron utility execution:
- /etc/crontab - on Debian-based systems
- /etc/anacrontab - on RedHat-based systems
- Anacron jobs definitions:
- /etc/cron.hourly/* - jobs run on an hourly basis
- /etc/cron.daily/* - jobs run on a daily basis
- /etc/cron.weekly/* - jobs run on a weekly basis
- /etc/cron.monthly/* - jobs run on a monthly basis
Anacrontab⌘
- Structure:
[period / period name] [delay] [job-identifier] [command]
- period - job is executed each period of days
- period name - job is executed daily, weekly, monthly, yearly or annualy
- delay - job is executed delay minutes after a full hour
- job-identifier - used to identify jobs in anacron messages
- command - command to be executed by anacron
Scheduling jobs to be run once⌘
- Configuration files:
- /etc/at.allow - contains new-line separated list of users allowed to run the at and batch commands
- /etc/at.deny - contains new-line separated list of users denied to run the at and batch command
- Management tools:
- at - queues job for later execution
- atq - lists users's pending jobs
- atrm - deletes user's pending job
- Lab Exercise 107.2
107.3 Localisation and internationalisation⌘
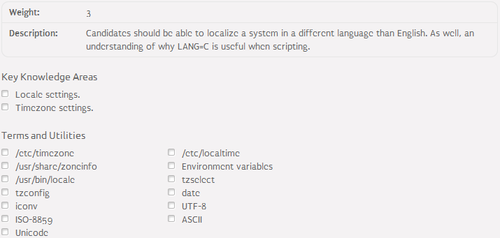
Encoding⌘
- Unicode:
- standard for consistent representation of text expressed in most of the world's writing systems
- character set - a list of characters with unique numbers
- Character encoding standards:
- ASCII - 7-bit encoding
- ISO-8859 - single-byte encoding
- UTF-8 - multi-byte encoding
- Encoding conversion - iconv
Locale⌘
- Locale - set of parameters that define user's language, country and other preferences
- Structure:
[language]_[territory].[codeset]@[modifier]
- language - language code
- territory - territory code
- codeset - encoding system
- modifier - optional parameters
- Management tools:
- locale - displays current locale
- locale-gen - generates locale
- Lab Exercise 107.3
Second Day - Session I⌘

108.1 Maintain system time⌘
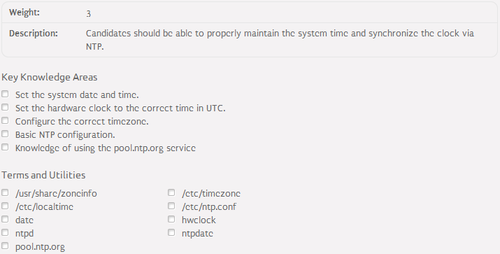
Basic concepts⌘
- Hardware Clock - maintains the time while the computer is turned off
- Software Clock - maintains the time while the computer is turned on
- GMT (Greenwich Mean Time) - local time in Greenwich adjusted for DST (Daylight Saving Time)
- UTC (Coordinated Universal Time) - local time in Greenwich not adjusted for DST
- Local Time - GMT adjusted for the time zone
- NTP (Network Time Protocol) - a protocol used for time adjustment over the network
Time, date and timezone configuration⌘
- Time and date manual configuration:
- hwclock - displays / configures hardware clock
- date - displays / configures software clock
- Timezone configuration:
- /usr/share/zoneinfo/* - contains timezones configuration files
- /etc/localtime:
- specifies timezone used by the system
- links into a file from /usr/share/zoneinfo directory
- /etc/timezone - specifies timezone name
- dpkg-recofigure tzdata - reconfigures timezone on Debian systems
- tzselect - reconfigures timezone on RedHat systems
NTP configuration⌘
- /etc/ntp.conf - main NTP configuration file:
- Client-side configuration and administration tools:
- pointing a client to the server via ntp.conf:
server [server]
- manual update of software time from the server:
ntpdate [server]
- Server-side configuration:
- ntpd - NTP server daemon
- ntpq - verifies NTP server operations
- pool.ntp.org - virtual cluster of publicly available and reliable time servers
- Lab Exercise 108.1
108.2 System logging⌘
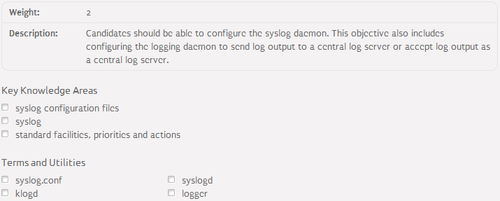
Syslog configuration⌘
- /etc/syslog.conf - main syslog configuration file:
- structure:
[facility].[priority] [action]
- facility:
- specifies a code word for the type of program or tool that generated the message to be logged
- valid codes: auth, authpriv, cron, daemon, kern, lpr, mail, mark, news, security, syslog, user, uucp, local[0-7], *
- priority:
- specifies a code word for the priority the message below which it is not logged
- valid codes: *, debug, info, notice, warning, warn, error, err, crit, alert, emerg, panic
- action:
- specifies a file into which the messages is logged
- a file can be a log file, device, remote syslog server ('@server') or all logged users ('*')
- facility:
- /etc/rsyslog.conf - main rsyslog configuration file
Syslog central log server⌘
- Client:
- point syslog daemon to send messages to the remote syslog server
[facility].[priority] @[server]
- Server:
- install syslog-ng package
- edit /etc/syslog-ng/syslog-ng.conf and include the following entries to accept all messages over the network:
source s_all {
udp();
};
...
log { source(s_all); filter(f_syslog3); destination(d_syslog); };
- perform additional configuration (man syslog-ng.conf)
Other logging tools⌘
- logger:
- used to create log entry manually
- example:
logger Sample Message
- klogd:
- reads and logs Linux kernel messages
- example:
klogd -o -f /var/log/kernel
- logrotate:
- used to automatically rotate logs
- Lab Exercise 108.2
108.3 Mail Transfer Agent (MTA) basics⌘
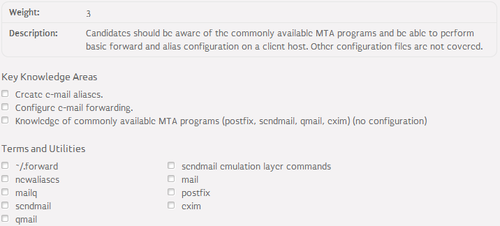
Email foundations⌘
- Email architecture:
- MUA (Mail User Agent) - formats user message in email format and submits it into the MSA
- MSA (Mail Submission Agent) - determines MTA into which an email should be send
- MTA (Mail Transfer Agent) - delivers an email into another MTA
- MDA (Mail Delivery Agent) - delivers an email into user mailbox
- Email protocols:
- SMTP (25) - used to send email between MTAs
- Submission (587) - used to send email from MUA to MSA
- POP3 (110) - used to get email from mailbox
- IMAP (143) - used to manage mailbox
- Email DNS records:
- MX - edge MTAs in the domain
- SPF - prevents email spoofing
MTA⌘
- The most popular Linux MTAs:
- Postfix - http://www.postfix.org/
- Exim - http://www.exim.org/
- Sendmail - http://www.sendmail.com/sm/open_source/
- Qmail - http://www.qmail.org/
- The most popular Linux colaboration suites with MTA:
- Zimbra - http://www.zimbra.com/
- Scalix - http://www.scalix.com/
Aliases⌘
- Define email address of system users
- /etc/aliases.db - aliases database
- /etc/aliases - aliases configuration file
- format:
[alias]: [email address | alias], [email address | alias], ...
- example:
postmaster: root root: IT@mycompany.com, MyCompanyIT@gmail.com
- newaliases - updates aliases database
MTA management⌘
- Management tools:
- mailq - displays mail queue
- mail - displays mailbox content
- ~/.forward - email forwarding configuration file:
- list of forwarders
- avoid infinite loops by using the '\' prefix
- Lab Exercise 108.3
108.4 Manage printers and printing⌘
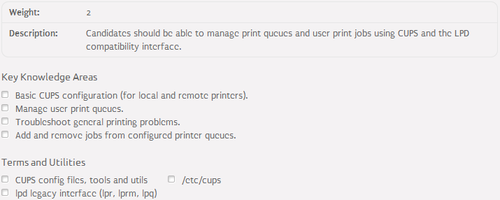
Print queue⌘
- Holding area where files wait to be printed
- /var/spool/cups/* - physical location of the print queue
- A single compute can support many distinct print queues
- Jobs are submitted to the print queue by the lpr program
- Can be managed in terms of jobs monitoring, ordering, deleting, etc.
- Network oriented - jobs can be submitted over the network
PostScript and Ghostscript⌘
- PostScript:
- printer language
- de facto standard for Linux
- Ghostscript:
- PostScript interpreter
- used for printers incompatible with PostScript
CUPS configuration⌘
- /etc/cups - main configuration directory:
- cupsd.conf - CUPS daemon configuration file
- printers.conf - printer definitions
- classes.conf - printer classes
- client.conf - CUPS client configuration
- lpoptions - printer options
- subscriptions.conf - active subscriptions
- ppd/* - additional options (PostScript Printer Definition)
- The easiest way to add a printer is to do it from the GUI
- CUPS web interface: http://localhost:631
CUPS management⌘
- Management tools:
- lpr - prints a file
- lpq - displays print queue status
- lpc - displays printers status
- lprm - removes a job from the print queue
- Lab Exercise 1.8.4
Second Day - Session II⌘

109.1 Fundamentals of internet protocols⌘
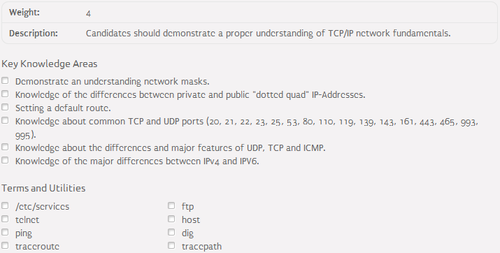
TCP/IP protocol stack⌘
MAC address⌘
- The most common link layer networks:
- Ethernet (802.1)
- WiFi (802.11)
- MAC (Media Access Control) address:
- used to uniquely identify a host in link layer
- 48 bits
- 12 hex values
- consists of:
- OUI (Organisationally Unique Identifier) - 24 bits
- NIC (Network Interface Controller) - 24 bits
- physically bound to the interface, but can be changed programmatically
- can coexist in 2 networks separated by a router
IP address⌘
- IP (Internet Protocol) address:
- used to uniquely identify a host in network layer
- 32 bits
- 4 decimal octests separated by dots
- consists of:
- Network Part delimited by a Subnet Mask
- Host Part delimited by a Subnet Mask
- special purpose addresses:
- network address
- broadcast address
- programmatically bound to the interface
- can not coexist in 2 networks separated by a router
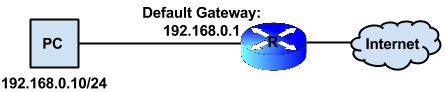
Default gateway⌘
IPv4 vs IPv6⌘
| Feature | IPv4 | IPv6 |
|---|---|---|
| IP address | 32 bits | 128 bits |
| Checksum | Header includes checksum | Header does not include checksum |
| Options | Header includes options | Extension headers |
| Broadcast IP address | Available | Not available; link-local IP address |
| IP address configuration | Manual or DHCP-based | Auto-configuration |
ICMP, TCP and UDP protocols⌘
- ICMP (Internet Control Message Protocol):
- used to send error messages between network hosts
- used to test network connectivity (ping)
- TCP (Transmission Control Protocol):
- the most widely used transport-layer protocol in the TCP/IP stack
- creates full connection for with error checking, acknowledgements, etc.
- used to ensure reliable data transmission
- UDP (User Datagram Protocol):
- best-effort transport-layer protocol
- does not create a connection between network hosts
- used in cases when reliable data transmission is not important or is provided by upper layer protocols
Network services⌘
| Port | Protocol | Service | Example Linux Implementation |
|---|---|---|---|
| 20 | TCP | FTP data | ProFTPd |
| 21 | TCP | FTP | ProFTPd |
| 22 | TCP | SSH | OpenSSH |
| 23 | TCP | Telnet | in.telnetd |
| 25 | TCP | SMTP | Postfix |
| 53 | TCP / UDP | DNS | BIND |
| 80 | TCP | HTTP | Apache |
| 110 | TCP | POP3 | Dovecot |
Network services #2⌘
| Port | Protocol | Service | Example Linux Implementation |
|---|---|---|---|
| 119 | TCP | NTTP | InterNetNews |
| 139 | TCP | Windows file sharing | Samba |
| 143 | TCP | IMAP | Dovecot |
| 161 | UDP | SNMP | Net-SNMP |
| 443 | TCP | HTTPS | Apache |
| 465 | TCP | SMTPS | Postfix |
| 993 | TCP | IMAPS | Dovecot |
| 995 | TCP | POP3S | Dovecot |
Basic IP configuration⌘
- Configuration files:
- /etc/protocols - IP protocols and their numbers
[protocol number] [protocol name] [protocol aliases] #[comment]
- /etc/services - TCP / UDP services and their ports
[service name] [port]/[protocol] [service aliases] #[comment]
- Lab Exercise 109.1
109.2 Basic network configuration⌘
Network interfaces configuration⌘
- Configuration files:
- /etc/network/interfaces - on Debian systems
- /etc/sysconfig/network-scripts/ifcfg-[interface name] - on RedHat systems
- Configuration tools:
- ifconfig - network interface configuration tool
- ifup - brings network interface up
- ifdown - brings network interfac down
Network interfaces configuration - Debian⌘
auto [interface name] iface [interface name] inet [dhcp | static] address [IP] netmask [SM] network [network IP] broadcast [broadcast IP] gateway [DG]
Network interfaces configuration - RedHat⌘
DEVICE=[interface name] ONBOOT=[no | yes] BOOTPROTO=[dhcp | none] IPADDR=[IP] NETMASK=[SM] NETWORK=[network IP] BROADCAST=[broadcast IP] GATEWAY=[DG]
Routing configuration⌘
- Manual:
- route command:
route add -net [network IP] netmask [SM] gw [next hop IP] [interface name]
- ip route command:
ip route add [network IP / SM] via [next hop IP] dev [interface name]
- Via configuration files:
- Debian (/etc/network/interfaces):
up [manual command]
- RedHat (/etc/sysconfig/network-scripts/route-[interface name]):
[network IP/ SM] via [next hop IP] dev [interface name]
- Lab Exercise 109.2
109.3 Basic network troubleshooting⌘
Network troubleshooting tools⌘
- host - simple DNS lookup tool
- dig - advance DNS lookup tool
- hostname - system hostname management tool
- ping - sends ICMP ECHO_REQUEST packet to network host
- traceroute - prints the route packets trace to network host
- tracepath - prints the route and MTU packets trace to network host
- telnet - establishes TCP session with any server
- ftp - establishes TCP session with FTP server
- Lab Exercise 109.3
109.4 Configure client side DNS⌘
NSS, resolver, DNS and hostname configuration⌘
- Resolver and DNS configuration files:
- /etc/nsswitch.conf - NSS (Name Service Switch) configuration file:
hosts: files dns
- /etc/hosts - resolver configuration file:
[IP] [domain name]
- /etc/resolv.conf - DNS (Domain Name System) configuration file:
search [domain 1] [domain 2] ... nameserver [IP 1] nameserver [IP 2] ...
- Hostname configuration file:
- /etc/hostname - on Debian-based systems
- /etc/sysconfig/network - on RedHat-based systems
- Hostname configuration file:
- Lab Exercise 109.4
Second Day - Session III⌘

110.1 Perform security administration tasks⌘
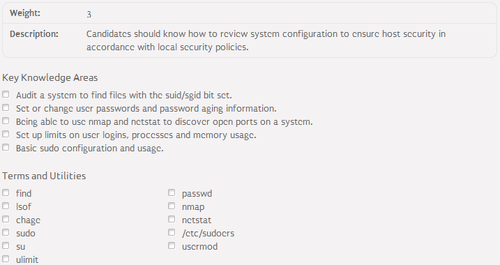
Security audit⌘
- Security audit definition (via searchcio.techtarget.com):
"A security audit is a systematic evaluation of the security of a company's information system by measuring how well it conforms to a set of established criteria."
- Security audit types:
- system scans
- network scans
- processes reviews
- policies reviews
- attacks
SUID and SGID bits⌘
- SUID (Set User ID):
- causes that users executing the program will inherit owner's permissions, UID and GID
- setup as an s character on third bit in standard access rights
- dangerous if an owner of the program is root
- SGID (Set Group ID):
- causes that newly created files and subdirectories in the directory will inherit GID
- setup as an s character on sixth bit in standard access rights
- dangerous if a group of the directory is root
- Finding files and directories with SUID and SGID bits setup:
find / -perm -u+s find / -perm -g+s
- Listing open files:
lsof
Password management⌘
- Changing user password:
passwd [username]
- Password and account expiration management:
- chage - used for password expiration management
- usermod - used for account expiration management
- examples:
- 1 year password expiration period:
chage -M 365 user
- 1 month account expiration period:
usermod -f 30 user
Network scans⌘
- nmap - scans open ports on a system by sending a bunch of TCP / UDP packets over the network:
- useful options:
- -p - specifies port, ports or a port range to scan
- -sU - specifies that UDP scan should be performed
- example:
- useful options:
nmap -p 80,443 google.com
- netstat - scans open ports on a local system by displaying a list of open sockets:
- useful options:
- -t - limits the output to show TCP connections only
- -a - shows both listening and non-listening sockets
- -p - shows PID of the process to which the socket belongs to
- -n - does not attempt to reverse resolve domain names
- example:
- useful options:
netstat -atpn | grep 631 | head -n 1 | awk '{print $7}'
Security limits⌘
- /etc/security/limits.conf - main security limits configuration file:
- structure:
[domain] [type] [item] [value]
- domain - username or group ('@')
- type - 'soft' or 'hard'
- item - system resource
- value - limit value
- ulimit - security limits management tool:
ulimit -a
Sudo configuration⌘
- Management tools:
- sudo - executes single command as another user
- su - switches into another user space
- gksudo / gksu - graphical versions of sudo / su
- visudo - used to edit /etc/sudoers file
- /etc/sudoers - sudo configuration file:
- example:
admin ALL=(ALL:ALL)NOPASSWD ALL
- explanation:
- admin - the rule applies to admin user
- first ALL - the user can run commands from any host
- second ALL - the user can run commands as any user
- third ALL - the user can run commands as any group
- NOPASSWD - the user does not need to type a password to run commands
- fourth ALL - the rule applies to any commands
- explanation:
- Lab Exercise 110.1
110.2 Setup host security⌘
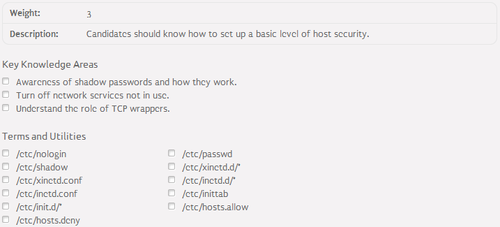
Super server⌘
- Listens for network connections on behalf of another program
- When a connection is initiated, hands off control of that connection to the intended server
- Reduces memory load if the super server handles many small servers that are seldom used
- Enhanced security thanks to the tcp wrappers
- Linux super servers:
- inetd - standard super server
- xinetd - enhanced super server
Inetd configuration⌘
- /etc/inetd.conf - main inetd configuration file:
- structure:
[service name] [socket type] [protocol] [wait / nowait] [user] [server name] [parameters]
- service name - name of the service from /etc/services file
- socket type - type of connection: stream, dgram, raw, seqpacket
- protocol - name of the protocol from /etc/protocols file
- wait / nowait - specifies whether all packets are processed before closing the socket
- user - username used to run the server
- server name - server executable path
- parameters - server parameters
- service inetd restart - restarts inetd super server
TCP wrapper⌘
- TCP wrapper - allows access to particular services from specified IP addresses only
- /usr/sbin/tcpd - TCP wrapper executable
- /etc/hosts.allow, /etc/hosts.deny - TCP wrapper configuration files:
- structure:
[daemon list]: [client list]
- daemon list - list of services from the /etc/services file
- client list - list of clients
- Running services via TCP wrapper:
[service name] [socket type] [protocol] [wait / nowait] [user] /usr/sbin/tcpd [server name] [parameters]
Xinetd configuration⌘
- /etc/xinetd.conf - main xinetd configuration file:
- structure:
service [service name]
{
socket_type = [socket type]
protocol = [protocol]
wait = no / yes
user = [user]
server = [server name]
server_args = [parameters]
only_from = [hosts.allow file path]
no_access = [hosts.deny file path]
}
- service xinetd restart - restarts xinetd super server
Additional security concerns⌘
- Listing unused network services:
netstat -tap
- Temporarily disabling login for non-root users:
- /etc/nologin
- file content is displayed and the loggin attempt fails
- Lab Exercise 110.2
110.3 Securing data with encryption⌘
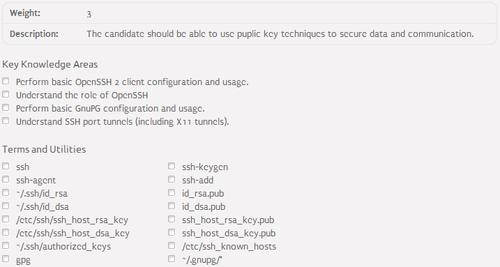
SSH⌘
- SSH (Secure SHell) - cryptographic network protocl to secure data communication
- SSH packages:
- openssh-server - SSH server
- openssh-client - SSH client
- SSH derivatives:
- SCP (Secure CoPy) - used to copy files over the network via SSH
- SSH Tunneling - used to wrap any kind of connection in an SSH
SSH architecture⌘
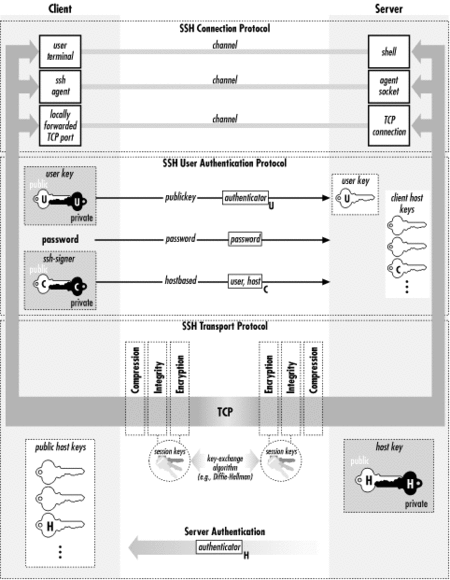
SSH configuration⌘
- /etc/ssh/ssh_config - main client configuration file
- /etc/ssh/sshd_config - main server configuration file
- /etc/ssh/ssh_host_rsa_key - host private RSA key
- /etc/ssh/ssh_host_rsa_key.pub - host public RSA key
- /etc/ssh/ssh_host_dsa_key - host private DSA key
- /etc/ssh/ssh_host_dsa_key.pub - host public DSA key
- ~/.ssh/id_rsa - user private RSA key
- ~/.ssh/id_rsa.pub - user public RSA key
- ~/.ssh/id_dsa - user private DSA key
- ~/.ssh/id_dsa.pub - user public DSA key
- ~/.ssh/known_hosts - server fingerprints accepted by a user
- ~/.ssh/authorized_keys - public keys of users allowed to SSH into the user account
SSH management⌘
- Management tools:
- ssh - runs SSH client
- ssh-keygen - used to create and manage private-public key pairs
- ssh-agent - program used to hold and remember the passphrace for private key
- ssh-add - adds user public key into the ~/.ssh/authorized_keys file
- SSH agent forwarding:
- /etc/ssh/ssh_config:
ForwardAgent yes
- /etc/ssh/sshd_config:
AllowAgentForwarding yes
SSH tunneling⌘
- /etc/ssh/sshd_config:
AllowTcpForwarding yes
- tunnel establishment:
ssh -N -f -L [local port]:[remote host]:[remote port] [username]@[remote host]
GPG⌘
- GPG (GNU Privacy Guard) - email encryption tool
- ~/.gnupg - user configuration directory
- GPG private-public key pair generation:
gpg --gen-key
- GPG public key export:
gpg --export [name] > [file]
- GPG public key import:
gpg --import [file]
- Listing GPG keys:
gpg --list
GPG usage⌘
- Encrypting data with GPG:
gpg --out [encrypted file] --recipient [UID] --armor --encrypt [decrypted file]
- Decrypting data with GPG:
gpg --out [decrypted file] --decrypt [encrypted file]
- Signing messages with GPG:
gpg --clearsign [file]
- Verifying signatures with GPG:
gpg --verify [file]
- Lab Exercise 110.3
Second Day - Session IV⌘

Certification and Surveys⌘
- Congratulations on completing the course!
- Official Certification:
- LPI: https://www.lpi.org
- Paerson VUE: http://www.pearsonvue.com/
- Prometric: https://www.prometric.com/en-us/Pages/home.aspx
- Visit http://www.nobleprog.com for other courses
- Surveys: http://www.nobleprog.pl/te

