RDS Patrick Custom
MySQL for Amazon RDS Training Course ⌘
A developer's primer on MySQL with RDS orientation.
About Us⌘
- Training & Consultancy Provider
- Founded in 2005
- Currently offering over 400 courses (remote & on-site)
- Continuously exapnding through franchishing opportunities
About Me⌘
- Consulting in IT & BI for 20 years
- CEO & Co-Founder of Craedone
- Analytics
- Business Intelligence
- Corporate Strategy/Red Team services
- Partnered with NobleProg since 2013
Expectations⌘
- customization vs. course standards
- content
- ugly slides
- SQL Server -> MySQL high-level
- Dialogue
MySQL Programs ⌘
- SERVER
- mysqld - the MySQL server
- mysqld_safe - a script which starts mysqld, recommended of starting the server
- restarts the server when an error occur
- logs run-time and failure information
- mysqld_multi - script that can start or stop multiple servers installed on the
system (different ports or sockets)
- CLIENT
- mysql - a command line client
- mysqladmin - administrative operations
- relading the grant tables
- creating/dropping database
- flushing tables to disk
- managing log files
- shutdown the database
MySQL Client⌘
- Windows [dev.mysql.com/downloads/windows/]
- MySQL Installer
- MySQL Connectors (drivers & connectivity)
- MySQL Workbench
- Excel Import/Export
- Ubuntu/Debian
- For Debian packages: [dev.mysql.com/downloads/repo/apt/]
- or...
apt-get install mysql-client
- OS X
- Native package: [dev.mysql.com/doc/refman/5.7/en/macosx-installation-pkg.html]
- Or try Homebrew: brew install mysql
We can get the RDS command line tools if we want:
AWS vs AWS⌘
EC2 vs RDS⌘
- This is not a pros/cons scale!
- driven by preference and tech needs
- direct cost comparisons are hard
|
EC2 |
RDS | ||
|
Pros |
Cons |
Pros |
Cons |
|
full admin control |
traditional admin tasks are time consuming |
less time on admin tasks |
no ssh (no tweaking) |
|
traditional SSH access and administration |
plan for more (logs, patching, etc.) |
automated patching/updates |
apps must not be version-dependant |
|
vertical scaling is easy |
more planning for resources |
very good performance out of the box |
some simple things become much more complex |
|
theoretically capable of better performance |
uesr management is good, but may not be intuitive | ||
|
debugging can be more work (logs) | |||
RDS Server Configuration⌘
Amazon’s relational database service [RDS] offers multiple platforms for their customers:
- MySQL
- Oracle
- SQL Server
- PostgreSQL
RDS is syntactically the same as the platforms it’s runs, but there are some minor differences in administrative concerns.
Benefits of RDS⌘
There are a number of factors that make RDS an attractive choice when evaluating relational databases for your architecture.
| Pre-configured (and reusable) parameters | DB Event notices (SMS or email) |
| Built-in monitoring and metrics | Multi-Availability Zone (off-site failovers) |
| Automatic updates/patches | Provisioned IOPS |
| Automated backups | Push-button scaling |
| Snapshot management | Automatic Host Replacements |
| Isolation & Security | Replication across Multi-AZ |
| Resource-level permissions | Programmable instance control |
Even Cheaper than RDS?⌘
Reserved instances ([pricing page]) are an option for RDS deployments known to be long-term solutions. From AWS: "Amazon RDS Reserved Instances give you the option to make a low, one-time payment for each DB instance you want to reserve and in turn receive a significant discount on the hourly charge for that instance."
- much cheaper than dynamic instances
| m3 type | reserved price/h | dynamic price/h | |
| single AZ | $0.089 | $0.090 | |
| multi AZ | $0.151 | $0.180 |
- can resell reserved instances through the marketplace
- comes in light/medium/heavy utilization groupings
- can still dynamically spin up or down multiple instances
- as long as you're in your reserved instance zone, the instances will assume your reserved pricing rates
- requires a one or three year commitment
The Server⌘
Deployment of all database instances in RDS can be managed through the Amazon Web Services (AWS) Console.
- no SSH access
- no direct log access
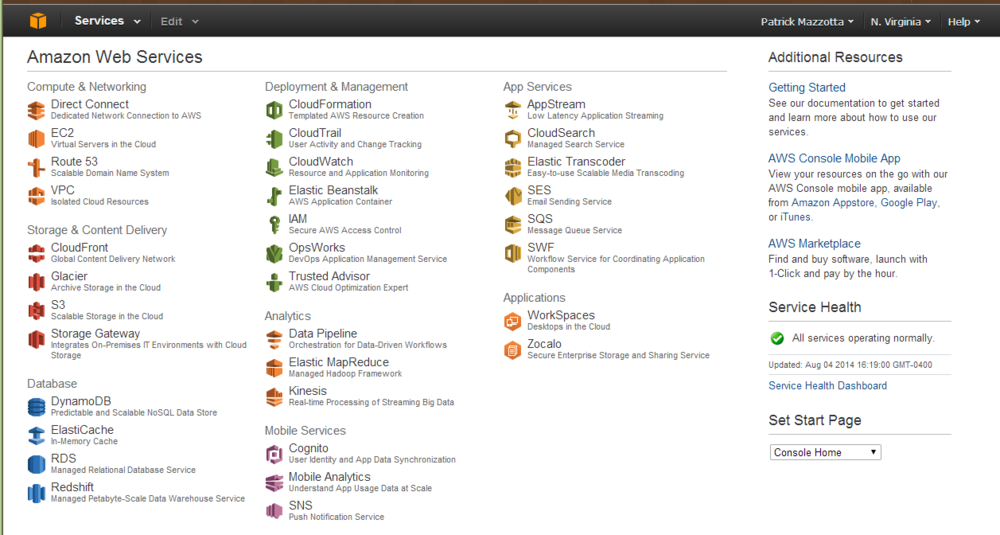
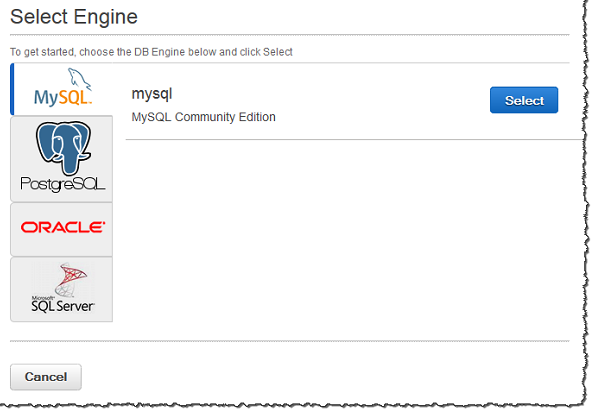
Launching MySQL Instance in RDS⌘
From [console.aws.amazon.com/rds/] we select the instance type.
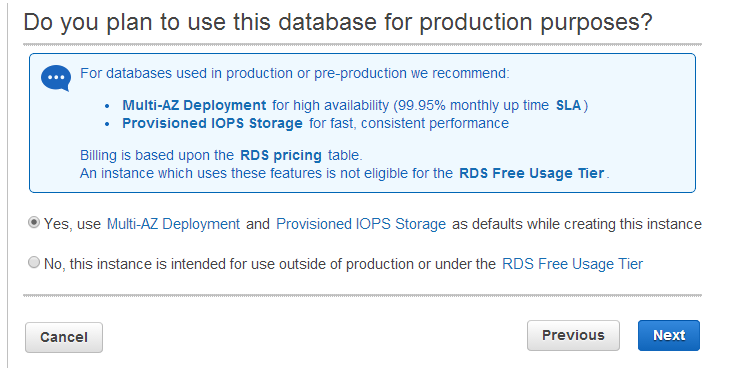
Deployment Type⌘
- When deploying an RDS instance you are asked if the instance is intended for production use or not.
- This tells AWS where the instance should go, and what kind of options should be made available (i.e. the Free Usage Tier lacks provisioning options).
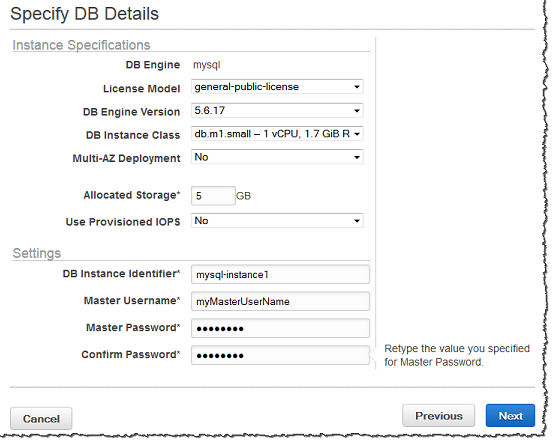
Specify DB Details⌘
DB Details Field Summary⌘
| Field | Description |
|---|---|
| License Model | MySQL has only one license model: general-public-license |
| DB Engine Version | Unless specifically required, you should select the default version of MySQL. Note that RDS supports different versions based on region of deployment. |
| DB Instance Class | This correlates directly with the instances in the RDS pricing table (see [aws.amazon.com/rds/pricing]). You should know [approximately] what class of instance you'll need before launching. |
| Multi-AZ Deployment | This instructs AWS to create a failover replica instance. Strongly recommended for production environments. |
| Allocated Storage | The amount of physical storage (in GB) your DB will be provisioned with. In some cases, allocating a higher amount of storage for your DB instance than the size of your DB can improve I/O performance (ref: [Amazon Relational Database Service Features]. |
| Use Provisioned IOPS | Provisioned IOPS (I/O operations Per Second) setting. This is typically used for high-performance storage needs in applications that are I/O intensive; such as transactional (OLTP) database workloads. |
| DB Instance Identifier | The name for the DB instance that is unique for your account in the region you selected. You may chose to add some intelligence to the name such as including the region and DB engine you selected, for example west2-mysql-instance1 [helpful for sysops work]. |
| Master Username | Type a name using alphanumeric characters that you will use as the master user name to log on to your DB instance. This will be the user name you use to logon to your DB on the instance for the first time. |
| Master Password/Confirmation | 8-16 ASCII characters (excluding /, *, and @) for your master user password. |
- Advanced settings: [RDS getting started page].
Security⌘
AWS Identity & Access Managment⌘
Identity and Access Management (IAM) is how we control access to AWS (and thereby RDS).
- it's a permission system
- rather elaborate (complicated but comprehensive)
- can manage access to:
- DB instances
- DB snapshots
- Read replicas
- Reserved instances
- DB security groups
- DB option groups
- DB parameter groups
- Event subscriptions
- DB subnet groups
- and all sorts of EC2 and other AWS stuff!
Standard IAM Practice⌘
- Create IAM users (user identities) under your AWS account for all users who will manage your Amazon RDS resources. Each user can have a separate password (for console access) and access keys (for programmatic and CLI access). You can organize IAM users into groups, which makes it easier to manage permissions for multiple users at a time.
- Determine what tasks each user and group will have regarding your Amazon RDS resources. For example, you could have groups for administrators, security personnel, DBAs, and developers.
- Optionally, you can tag the Amazon RDS resources you want to control access to. You can assign a tag, a key-value pair, to any Amazon RDS resource, and use that tag as a way to specify a particular resource in an IAM policy..
- Create the IAM policies that define the actions a user can take, and specify the Amazon RDS resources required for each task using Amazon Resource Names (ARNs). If you have used tags for your Amazon RDS resources, you can add conditions to the policy to test for those tag values.
- Attach the policies to the applicable users or groups.
IAM Policies⌘
IAM Policies (con't)⌘
- By default newly created IAM users do not have permission to access any AWS resources
- users require IAM policies to access the required Amazon RDS API (or any AWS) actions and resources
- policies can be attached to users, groups, or roles
- An IAM policy is a JSON document that consists of one or more statements
{
"Version":"2012-10-17",
"Statement":[{
"Effect":"Allow",
"Action": "rds:CreateDBInstance",
"Resource":"arn:aws:rds:us-east-1:1234567890:db:test*",
"Condition": {"streq":[
{"rds:DatabaseEngine":"mysql"},
{"rds:DatabaseClass":"db.t1.micro"}
]}
}]
}
- The Version is required, and the value should be "2012-10-17"
- this is the date of the most current version of the AWS IAM policy system
- The Effect element is set to either "Allow" or "Deny"
- Actions are denied by default, so you have to specify "Allow"
- The Action element lists which AWS APIs the policy will allow.
- here the Action element lists one action from the Amazon RDS API - so it will be the only action allowed by this policy statement
- Note that the action is identified by both service name (rds) and action (CreateDBInstance)
- policies can list actions from any AWS service. You can use wildcards (*) to specify actions
- i.e. the action rds:Describe* would allow the user to perform any Amazon RDS action that begins with Describe (DescribeDBInstances, DescribeDBLogFiles, DescribeDBParameterGroups,DescribeDBSnapshots, etc.)
- The Resource element lets you specify which resources the user can perform the actions on or with
- here the user can only create DB instances that have the prefix "test" in the DB instance name
- You specify resources using an Amazon Resources Name (ARN) that includes the name of the service that the resource belongs to (rds), the region (us-east-1), the account number, and the type of resource (a DB instance)
- Finally, the optional Condition element lets you specify additional restrictions on the policy such as:
- date/time
- source IP address
- region
- tags
- In this example the Condition element indicates that the actions are allowed only on instances with the MySQL DB engine and the micro DB instance class
Attaching Policies⌘
Policies can be attached to
- an individual IAM user
- in this case, only that user would be allowed to perform the listed actions
- an IAM group
- then every IAM user in that group would have these permissions
- or a role
- where delegated or federated users could perform the action
Users vs. Roles vs. Groups⌘
- Users
- have permanent long-term credentials
- are used to directly interact with AWS services
- Roles
- do not have any credentials
- cannot make direct requests to AWS services
- meant to be "assumed" by authorized entities, such as IAM users, applications, or an AWS service like EC2
- Groups
- are a collection of IAM users that share the same permissions
- primarily a management convenience to manage the same set of permissions for a set of IAM users
- groups cannot have roles added to themselves (yet)
Can I Haz Consoles?⌘
The following example policy statement shows permissions that users typically need in order to work in the Amazon RDS console. Notice that this includes RDS actions that start with the word "Describe," a number of EC2 and CloudWatch actions that likewise pertain to describing (listing) resources, and all SNS actions.
{
"Version":"2012-10-17",
"Statement":[{
"Effect": "Allow",
"Action": [
"rds:Describe*",
"rds:ListTagsForResource",
"ec2:DescribeAvailabilityZones",
"ec2:DescribeVpcs",
"ec2:DescribeAccountAttributes",
"ec2:DescribeSecurityGroups",
"ec2:DescribeSubnets",
"cloudwatch:GetMetricStatistics",
"cloudwatch:DescribeAlarms",
"sns:*"
],
"Resource": "*"
}]
}
Authorization Request Chain⌘
- an IAM authorization request is generated for each resource identified (or implied) in the request
- easy to trigger multiple resource authorizations, i.e.a point-in-time-restore to a new database instance will generate two authorization requests:
- An authorization request will be generated for the target database instance.
- An authorization request will be generated for the snapshot that is being restored
- a policy can be used to limit the possible values a resource can have
- i.e. storage or compute size can be limited to specific values or ranges.
- More elaborate coverage of [IAM Policy Evaluation Logic here]
Keys and Tags⌘
When creating an IAM policy, you can specify conditions in two ways
- You can create a condition that is based on a tag associated with a resource
- You can use a predefined key, such as the DB engine type or the DB engine class.
The following tables shows the predefined keys you can use when defining IAM policy for Amazon RDS. Note that tag key/value pairs and predefined keys are case sensitive.
Predefined Keys (AWS)⌘
| AWS Predefined Key | Description | Value Type |
|---|---|---|
| aws:CurrentTime | The current time. Used for date conditions. | Date/Time |
| aws:EpochTime | The current time in epoch or UNIX time format. Used for date conditions. | Date/Time |
| aws:principaltype | The type of principal (user, account, federated user, etc.) for the current request. | String |
| aws:SourceIp | The requester's IP address (see IP Address ). Note that if you use aws:SourceIp, and the request comes from an Amazon EC2 instance, the instance's public IP address is evaluated. | IP Address |
| aws:UserAgent | The requester's client application. | String |
| aws:userid | The requester's user ID. | String |
| aws:username | The requester's user name | String |
Predefined Keys (RDS)⌘
Amazon RDS also has predefined keys that you can include in Condition elements in an IAM policy. Amazon RDS predefined keys do not apply to all actions; the Amazon RDS predefined keys apply to the following actions:
- CreateDBInstance
- ModifyDBInstance
- DeleteDBInstance
- DescribeDBLogFiles
- AddTagsToResource
- RemoveTagsFromResource
- RestoreDBInstanceToPointInTime
- RestoreDBInstanceFromDBSnapshot
- DownloadDBLogFilePortion
- DescribeDBInstances
| RDS Predefined Key | Description | Value Type |
|---|---|---|
| rds:DatabaseClass | The DB instance class of a DB instance | String |
| rds:DatabaseEngine | The DB engine of the DB instance | String |
| rds:DatabaseName | The name of the database on the DB instance | String |
| rds:MultiAz | Indicates if the DB instance is running in multiple availability zones. 1 indicates that the DB instance is using multi-AZ. | Integer |
| rds:Piops | This key will be present when a request is made for a DB instance with PIOPs enabled. The value will contain the number of provisioned IOs that an instance supports. 0 indicates does not have PIOPs enabled. | Integer |
| rds:StorageSize | The storage volume size (in GB) | Integer |
| rds:Vpc | Indicates if the database instance is running in a virtual private cloud | Boolean |
Conditional Elements⌘
You can add your own tags to an Amazon RDS resource and then create policies that use the tag values in determining whether to grant or deny access. Amazon RDS resource tags are formatted slightly differently than predefined keys in aCondition element. For example, the following Condition element uses a predefined key and specifies that the condition applies to the DB engine MySQL:
"Condition":{"streq":{"rds:DatabaseEngine": "mysql" } }
The following Condition element uses an Amazon RDS tag and specifies that the condition applies to a tag with a key named environment and a value of production.
"Condition":{"streq":{"rds:db-tag/environment": ["production"]} }
More on the IAM policy Condition element [here]
Example IAM Policies for RDS⌘
Example 1: Permit a user to perform any Describe action on any RDS resource⌘
The following statement allows a user to run all the actions whose names begin with "Describe," which shows information about an RDS resource such as a DB instance. Note that the “*” in the Resource element indicates that the actions are allowed for all Amazon RDS resources.
{
"Version":"2012-10-17",
"Statement":[{
"Effect":"Allow",
"Action":"rds:Describe*",
"Resource":"*"
}]
}
Example 2: Permit a user to create a DB instance that uses a specified DB engine⌘
The following statement uses a predefined Amazon RDS key and allows a user to create only DB instances that use the MySQL DB engine. The Condition element indicates that the DB engine requirement is MySQL.
{
"Version":"2012-10-17",
"Statement":[{
"Effect":"Allow",
"Action": "rds:CreateDBInstance",
"Resource": "*",
"Condition":{"strneq":{"rds:DatabaseEngine":"mysql"}}
}]
}
Example 3: Permit a user to create a DB instance that uses the specified DB parameter and security groups⌘
The following statement allows a user to only create a DB instance that must use the mysql-production DB parameter group and the db-production DB security group.
{
"Version":"2012-10-17",
"Statement":[{
"Effect":"Allow",
"Action": "rds:CreateDBInstance",
"Resource": [
"arn:aws:rds:us-east-1:1234567890:pg:mysql-production",
"arn:aws:rds:us-east-1:1234567890:secgrp:db-production" ]
}]
}
Example 4: Prevent a user from creating a DB instance that uses specified DB parameter groups⌘
The following statement prevents a user from creating a DB instance that uses DB parameter groups with specific tag values. You might apply this policy if you require that a specific customer-created DB parameter group always be used when creating DB instances. Note that statements that use Deny are most often used to restrict access that was granted by a broader statement.
{
"Version":"2012-10-17",
"Statement":[{
"Effect":"Deny",
"Action": "rds:CreateDBInstance",
"Resource": "*",
"Condition": {"streq": {"rds:db-tag/usage" : "prod" } }
}]
}
Example 5: Prevent users from creating DB instances for certain DB instance classes and from creating DB instances that use Provisioned IOPS⌘
The following statement prevents users from creating DB instances that use the DB instance classes m2.2xlarge and m2.4xlarge, which are the largest and most expensive instances. This example also prevents users from creating DB instances that use Provisioned IOPS, which is an additional cost.
{
"Version":"2012-10-17",
"Statement":[
{
"Effect":"Deny",
"Action":"rds:CreateDBInstance",
"Resource": "*",
"Condition":{"streq":{"rds:DatabaseClass":["db.m2.4xlarge", "db.m2.2xlarge"]}}
},
{
"Effect":"Deny",
"Action":"rds:CreateDBInstance",
"Resource": "*",
"Condition":{"NumericNotEquals":{"rds:Piops":"0"}}
}
]
}
You can add a tag to an Amazon RDS resource, and then use that tag in a policy to specify a particular resource. The following examples use Amazon RDS resource tags as part of the IAM policy to specify a particular resource.
Example 6: Permits a user to perform an action on a resource tagged with two different values⌘
This following statement allows a user to perform the ModifyDBInstance and CreateDBSnapshot actions on instances with either the “stage” tag set to “development” or “test.”
{
"Version":"2012-10-17",
"Statement":[{
"Effect":"Allow",
"Action": [
"rds:ModifyDBInstance",
"rds:CreateDBSnapshot" ],
"Resource":"*",
"Condition":{"streq":{"db-tag/stage": [ "development", "test" ] } }
}]
}
Example 7: Permits a user to perform actions on a DB instance with a DB instance name prefixed with the user name⌘
This following statement allows a user to perform any action (except to add or remove tags) on a DB instance that has a DB instance name that is prefixed with the user's name and that has a tag called "stage" equal to "devo" or that has no tag called "stage."
{
"Version":"2012-10-17",
"Statement":[{
"Effect":"Allow",
"NotAction": ["rds:AddTagsToResource","rds:RemoveTagsFromResource"],
"Resource": "arn:aws:rds:*:314195462963:db:${aws:username}*",
"Condition":{"StringEqualsIfExists":{"rds:db-tag/stage":"devo"}}
}]
}
RDS Security Groups⌘
Security groups control the access that traffic has in and out of a DB instance.
Three types of security groups are used with Amazon RDS:
- DB security groups
- VPC security groups (virutal private
networkcloud) - EC2 security groups
DB Security Groups⌘
Each DB security group rule enables a specific source to access a DB instance that is associated with that DB security group. The source can be a range of addresses (e.g., 203.0.113.0/24), or an EC2 security group. When you specify an EC2 security group as the source, you allow incoming traffic from all EC2 instances that use that EC2 security group. Note: DB security group rules apply to inbound traffic only; outbound traffic is not currently permitted for DB instances.
- You do not need to specify a destination port number when you create DB security group rules; the port number defined for the DB instance is used as the destination port number for all rules defined for the DB security group.
- DB security groups can be created using the Amazon RDS APIs or the Amazon RDS page of the AWS Management Console.
VPC Security Groups⌘
- Each VPC security group rule enables a specific source to access a DB instance in a VPC that is associated with that VPC security group.
- The source can be a range of addresses (e.g., 203.0.113.0/24), or another VPC security group
- specifying a VPC security group as the source allows incoming traffic from all instances (typically application servers) that use the source VPC security group
- VPC security groups can have rules that govern both inbound and outbound traffic, though the outbound traffic rules do not apply to DB instances
- Note: you must use the Amazon EC2 API or the Security Group option on the VPC Console to create VPC security groups.
- DB instances deployed within a VPC can be configured to be accessible from the Internet or from EC2 instances outside the VPC
- if a VPC security group can specify a port access such as TCP port 22 you will not be able to access the DB instance
- the firewall for the DB instance provides access only via the IP addresses specified by the DB security groups the instance is a member of and the port defined when the DB instance was created
- if a VPC security group can specify a port access such as TCP port 22 you will not be able to access the DB instance
You should use TCP as the protocol for any VPC security group created to control access to a DB instance. The port number for the VPC security group should be the same port number as that used to create the DB instance.
DB Security Groups vs. VPC Security Groups⌘
The following table shows the key differences between DB security groups and VPC security groups.
| DB Security Group | VPC Security Group |
|---|---|
| Controls access to DB instances outside a VPC | Controls access to DB instances in VPC. |
| Uses Amazon RDS APIs or Amazon RDS page of the AWS Management Console to create and manage group/rules | Uses Amazon EC2 APIs or Amazon VPC page of the AWS Management Console to create and manage group/rules. |
| When you add a rule to a group, you do not need to specify port number or protocol. | When you add a rule to a group, you should specify the protocol as TCP, and specify the same port number that you used to create the DB instances (or Options) you plan to add as members to the group. |
| Groups allow access from EC2 security groups in your AWS account or other accounts. Groups allow access from other VPC security groups in your VPC only. |
Security Group Scenario⌘
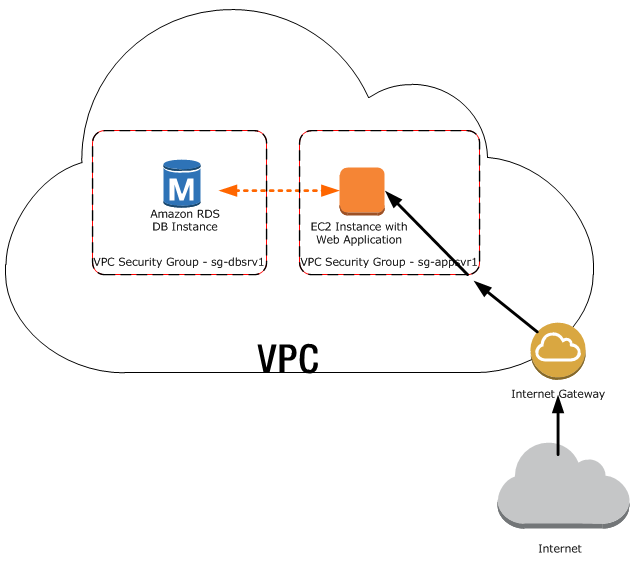
A common use of an RDS instance in a VPC is to share data with an application server running in an EC2 instance in the same VPC and that is accessed by a client application outside the VPC. For this scenario, you would do the following to create the necessary instances and security groups. You can use the RDS and VPC pages on the AWS Console or the RDS and EC2 APIs.
- Create a VPC security group (for example, "sg-appsrv1") and define inbound rules that use as source the IP addresses of the client application. This security group allows your client application to connect to EC2 instances in a VPC that uses this security group.
- Create an EC2 instance for the application and add the EC2 instance to the VPC security group ("sg-appsrv1") you created in the previous step. The EC2 instance in the VPC shares the VPC security group with the DB instance.
- Create a second VPC security group (for example, "sg-dbsrv1") and create a new rule by specifying the VPC security group you created in step 1 ("sg-appsrv1") as the source.
- Create a new DB instance and add the DB instance to the VPC security group ("sg-dbsrv1") you created in the previous step. When you create the instance, use the same port number as the one specified for the VPC security group ("sg-dbsrv1") rule you created in step 3.
The following diagram shows this scenario.
Security Group Scenario⌘
Working with DB Security Groups⌘
A DB security group controls network access to a DB instance that is not inside a VPC. By default, network access is turned off to a DB instance. You can specify rules in a security group that allows access from an IP address range, port, or EC2 security group. Once ingress rules are configured, the same rules apply to all DB instances that are associated with that security group. You can specify up to 20 rules in a security group.
If you are a new customer to Amazon RDS or if you are an existing customer who is using a new region, your DB instance is most likely in a default VPC. You cannot use a DB security group for a DB instance inside a VPC; you must create a VPC security group. For information on creating a VPC security group, see Security Groups for Your VPC. To determine if you have a default VPC, see step 2 in the following procedure. Read More:
- [Creating a DB Security Group]
- [Listing Available DB Security Groups]
- [Viewing a DB security group]
- [Authorizing Network Access to a DB Security Group from an IP Range]
- [Authorizing Network Access to a DB Instance from an Amazon EC2 Instance]
- [Revoking Network Access to a DB Instance from an IP Range]
- [Related Topics]
Creating DB Security Groups⌘
To create a DB security group, you need to provide a name and a description.
From AWS Management Console:
- Sign in to the AWS Management Console and open the Amazon RDS console at https://console.aws.amazon.com/rds/.
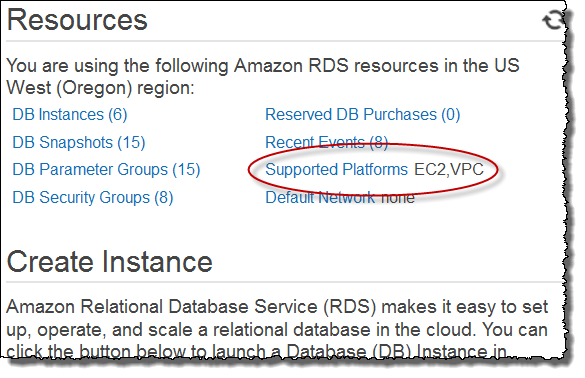
- Determine what platforms are supported for your AWS account in your current region.
If Supported Platforms indicates EC2,VPC, your AWS account in the current region does not use a default VPC. You can continue following the steps below to create a DB security group that will enable access to your DB instance.
Creating DB Security Group (con't)⌘
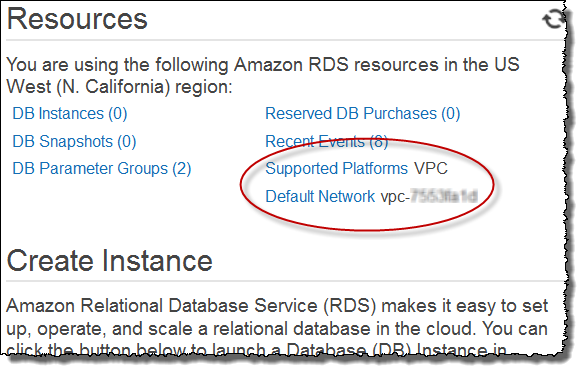
If Supported Platforms indicates VPC, your AWS account in the current region uses a default VPC. This means that you must create a VPC security group to enable access to a DB instance instead of a DB security group. For information on creating a VPC security group, see [Security Groups for Your VPC].
Creating DB Security Group (con't)⌘
- Click Security Groups in the navigation pane on the left side of the window.
- Click Create DB Security Group.
Creating DB Security Group (con't)⌘
- Type the name and description of the new DB security group in the Name and Description text boxes. Note that the security group name cannot contain spaces and cannot start with a number.
- Click Yes, Create. The DB security group will be created. Note that a newly created DB security group does not provide access to a DB instance by default. You must specify a range of IP addresses or an Amazon EC2 security group that can have access to the DB instance. To specify IP addresses or an Amazon EC2 security group for a DB security group, see Authorizing Network Access to a DB Security Group from an IP Range.
Creating DB Security Group (CLI)⌘
Use the command rds-create-db-security-group with the following parameters:
$>rds-create-db-security-group mydbsecuritygroup -d "My new security group"
Note that a newly created DB security group does not provide access to a DB instance by default. You must specify a range of IP addresses or an Amazon EC2 security group that can have access to the DB instance. To specify IP addresses or an Amazon EC2 security group for a DB security group, see [Authorizing Network Access to a DB Security Group from an IP Range].
Creating DB Security Group (API)⌘
- Call CreateDBSecurityGroup with the following parameters:
- DBSecurityGroupName = mydbsecuritygroup
- Description = "My new security group"
https://rds.amazonaws.com/ ?Action=CreateDBSecurityGroup &DBParameterGroupName=mydbsecuritygroup &Description=My%20new%20db%20security%20group &Version=2012-01-15 &SignatureVersion=2 &SignatureMethod=HmacSHA256 &Timestamp=2012-01-20T22%3A06%3A23.624Z &AWSAccessKeyId=<AWS Access Key ID> &Signature=<Signature>
Note that a newly created DB security group does not provide access to a DB instance by default. You must specify a range of IP addresses or an Amazon EC2 security group that can have access to the DB instance. To specify IP addresses or an Amazon EC2 security group for a DB security group, see [Authorizing Network Access to a DB Security Group from an IP Range].
Listing Available DB Security Groups⌘
You can list which DB security groups have been created for your AWS account.
- AWS Console
- Sign in to the AWS Management Console and open the Amazon RDS console athttps://console.aws.amazon.com/rds/.
- Click Security Groups in the navigation pane on the left side of the window.
- The available DB security groups appear in the DB Security Groups list.
- CLI
- Use the command rds-describe-db-security-groups to list all available DB security groups for your AWS account
PROMPT>rds-describe-db-security-groups
- API
- Call DescribeDBSecurityGroups with no parameters
https://rds.amazonaws.com/ ?Action=DescribeDBSecurityGroups &MaxRecords=100 &Version=2009-10-16 &SignatureVersion=2 &SignatureMethod=HmacSHA256 &AWSAccessKeyId=<AWS Access Key ID> &Signature=<Signature>
Viewing DB Security Group⌘
You can view detailed information about your DB security group to see what IP ranges have been authorized.
- AWS Console - select the details icon for the DB security group you want to view
- CLI - use the rds-describe-db-security-groups to view a DB security group specifying the DB security group you want to view
PROMPT>rds-describe-db-security-groups <mydbsecuritygroup>
- API - call DescribeDBSecurityGroups with the parameter DBSecurityGroupName = <mydbsecuritygroup>
https://rds.amazonaws.com/ ?Action=DescribeDBSecurityGroups &DBParameterGroupName=mydbsecuritygroup &Version=2009-10-16 &SignatureVersion=2 &SignatureMethod=HmacSHA256 &Timestamp=2009-10-16T22%3A23%3A07.107Z &AWSAccessKeyId=<AWS Access Key ID> &Signature=<Signature>
SSL⌘
Amazon RDS supports SSL connections with DB instances running the MySQL database engine.
- Amazon RDS creates an SSL certificate and installs the certificate on the DB instance when Amazon RDS provisions the instance
- These are signed by a certificate authority. The SSL certificate includes the DB instance endpoint as the Common Name (CN) for the SSL certificate to guard against spoofing attacks. The public key is stored at https://rds.amazonaws.com/doc/mysql-ssl-ca-cert.pem.
- To encrypt connections using the default mysql client, launch the mysql client using the --ssl_ca parameter to reference the public key, for example:
mysql -h myinstance.c9akciq32.rds-us-east-1.amazonaws.com --ssl_ca=rds-ssl-ca-cert.pem --ssl-verify-server-cert
- You can use the GRANT statement to require SSL connections for specific users accounts. For example, you can use the following statement to require SSL connections on the user account encrypted_user:
GRANT USAGE ON *.* TO 'encrypted_user'@'%' REQUIRE SSL
And many more!⌘
- most of the controls you need can be found in the AWS/RDS console
- API documentation at [http://docs.aws.amazon.com/AmazonRDS/latest/APIReference/Welcome.html]
- CLI documentation at [http://docs.aws.amazon.com/AmazonRDS/latest/CommandLineReference/Welcome.html]
NOTE
- You can't authorize an Amazon EC2 security group that is in a different AWS Region than your DB instance
- By default network access is turned off to a DB instance - if you want to access a DB instance that is not in a VPC, you must set access rules for a DB security group to allow access from specific EC2 security groups
- revoking rules and permissons aren't always immediate (users vs ingress rules)
MySQL Log Files⌘
MySQL Logging Formats⌘
Binary log traditionally uses three formats:
- Replication capabilities in MySQL originally were based on propagation of SQL statements from master to slave. This is called statement-based logging. You can cause this format to be used by starting the server with --binlog-format=STATEMENT.
- In row-based logging, the master writes events to the binary log that indicate how individual table rows are affected. You can cause the server to use row-based logging by starting it with --binlog-format=ROW.
- A third option is also available: mixed logging. With mixed logging, statement-based logging is used by default, but the logging mode switches automatically to row-based in certain cases as described below. You can cause MySQL to use mixed logging explicitly by starting mysqld with the option --binlog-format=MIXED.
"With statement-based replication, there may be issues with replicating nondeterministic statements. In deciding whether or not a given statement is safe for statement-based replication, MySQL determines whether it can guarantee that the statement can be replicated using statement-based logging. If MySQL cannot make this guarantee, it marks the statement as potentially unreliable and issues the warning 'Statement may not be safe to log in statement format.'"
Logging in RDS⌘
- all access is through AWS console or configured through AWS console
- Amazon RDS supports mixed and row-based binary logging (version-dependant)
- viewing and listing logs: [DRY]
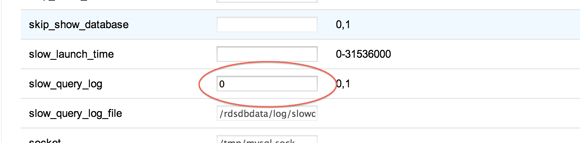
Slow Query Log⌘
- enable via DB Parameters in the RDS console
- default setting for long_query_time is 10 seconds
- query against mysql.slow_log
- rotate the "log" by calling stored procedure CALL rds_rotate_slow_log
- can log queries that are faster than the long_query_time by enabling log_queries_not_using_indexes
You can monitor the MySQL error log, slow query log, and the general log directly through the Amazon RDS console, Amazon RDS API, Amazon RDS CLI, or AWS SDKs. You can use the mysqlbinlog utility to download or stream a binary log. The MySQL error log is generated by default; you can generate the slow query and general logs by setting parameters in your DB parameter group. Amazon RDS rotates all of the MySQL log files, the intervals for each type are given below
So how to manage it?⌘
- Splunk
- Logstash
- old-school
MySQL vs. SQL Server⌘
Advantages of Mysql over SQL Server in RDS⌘
Or, "Preaching to the choir".
- Read-Replicas: You can utilize the mysql built-in replication features For read-heavy database workloads by creating Read Replicas.
- Availability: To increase database availability you could use the Multi-azfeature.In the event of DB Instance failure or an Availability Zone failure, Amazon RDS will automatically failover to the standby so that database operations.
- VPC's: Only Mysql instances can be configured in VPC.With Amazon VPC, you can define a virtual network topology and customize the network configuration to closely resemble a traditional network that you might operate in your own datacenter.
- High SLA: Amazon RDS recently came out of Beta and also offered a higher SLA(99.95%) for Multi-az instances which is currently available only for MysQl and Oracle
Amazon RDS SLA
The Comp Train⌘
The following slides compare the different platforms and related features. Where possible, some best practices are included.
|
Standard |
The latest official version of SQL is SQL:2008. |
|
MS SQL Server 2005 on Windows XP. Microsoft's SQL implementation is sometimes namedTransact-SQL, or TSQL. In this document, I'll generally write MSSQL as a short-hand for Microsoft's SQL Server product. | |
|
MySQL Database Server 5.0.18 on Fedora Linux (i.e. MySQL AB's "classic" DBMS product�not MaxDB). |
The products are running with their default settings. This is important for MySQL and MSSQL: Their interpretation of SQL may be changed rather drastically by adjusting certain configuration options, potentially increasing the level of standard
Views⌘
|
Standard |
Views are part of the standard, and they may be updated, as long as it 'makes sense'.SQL:2008 has a rather complicated set of rules governing when a view is updatable, basically saying that a view is updatable, as long as the update-operation translates into an unambiguous change.SQL-92 was more restrictive, specifying that updatable views cannot be derived from more than one base table. |
|
MSSQL |
Conforms to at least SQL-92. |
|
MySQL |
Conforms to at least SQL-92. |
Join types and features⌘
All the DBMSes support basic INNER JOINs, but vary in their support for other join types. In the following feature chart, a ✓ means yes; an empty table cell means no.
|
Join type/feature |
MSSQL |
MySQL |
|
Natural joins (only tested: |
✓ | |
|
|
✓ | |
|
FULL joins1 (tested: |
✓ | |
|
Explicit |
✓ | ✓ |
Note that FULL joins may be emulated with a union of a left and a right join.
Copying structure⌘
Objective: An existing table, t1 needs to be copied to a new table, t2, without copying data. I.e., only the structure/definition of the table is copied.
|
Standard |
Optional feature T171 defines LIKE clause in table definition: |
|
MSSQL |
Does not support the standard. Instead, MSSQL has a special |
|
MySQL |
Complies with the core of the feature (T171), but not with the extended features (T173).MySQL does not allow you to copy the structure of a view into a table. |
Ordering result sets⌘
|
Standard |
The SQL-standard states that relations are unordered, but result sets may be ordered when returned to the user through a cursor: |
|
MSSQL |
As well as in cursor definitions, it allows |
|
MySQL |
As well as in cursor definitions, it allows |
Simple limit⌘
Objective: Want to only get n rows in the result set. Usually only makes sense in connection with an ORDER BY expression.
Note: This is not the same as a top-n query � see next section. Also: Some of the queries below may not be legal in all situations, such as in views or sub-queries. Read more at Use The Index, Luke!
|
Standard |
The SQL standard provides three ways of performing a 'simple limit':
|
|
MSSQL |
Supports the |
|
MySQL |
Doesn't support the standard. Alternative solution: |
=Top-n query⌘
Objective: Like the simple limit-query above, but include rows with tie conditions. Thus, the query may return more than n rows. Some call this a quota-query. The following examples are based on this table:
SELECT * FROM person ORDER BY age ASC; +----------+-------------+-----+ |PERSON_ID | PERSON_NAME | AGE | +----------+-------------+-----+ | 7 | Hilda | 12 | | 8 | Bill | 12 | | 4 | Joe | 23 | | 2 | Veronica | 23 | | 3 | Michael | 27 | | 9 | Marianne | 27 | | 1 | Ben | 50 | | 10 | Michelle | 50 | | 5 | Irene | 77 | | 6 | Vivian | 77 | +----------+-------------+-----+
Now, we only want the three (n=3) youngest persons displayed, i.e. a result set like this:
+----------+-------------+-----+ |PERSON_ID | PERSON_NAME | AGE | +----------+-------------+-----+ | 7 | Hilda | 12 | | 8 | Bill | 12 | | 4 | Joe | 23 | | 2 | Veronica | 23 | +----------+-------------+-----+
=Top-n query (con't)⌘
|
Standard |
With standard SQL, there are two principal ways to obtain the wanted data:
|
|
MSSQL |
Supports the fast standard SQL variant.MSSQL 2000 supported the slow standard SQL variant. In practice, a MSSQL-only expression had to be used instead, in order to obtain acceptable query performance: |
|
MySQL |
Supports the slow standard SQL solution. In practice, this MySQL-specific solution should be used instead, in order to obtain acceptable query performance: |
Limit with offset⌘
Objective: Want to only get n rows in the result set, and we want the first skip rows in the result set discarded. Usually only makes sense in connection with an ORDER BY expression.
In the recipes below, basic ordering is ASCending, i.e. lowest-first queries. If you want the opposite, then change ASC->DESC and DESC->ASC at the places emphasized like this.
|
Standard |
The SQL standard provides three ways of performing 'limit with offset':
|
|
MSSQL |
Supports the window function and cursor based approaches.MSSQL 2000 didn't support |
|
MySQL |
Doesn't support the standard approaches. Alternative solution: |
Inserting several rows at a time⌘
|
Standard |
An optional SQL feature is row value constructors (feature ID F641). One handy use of row value constructors is when inserting several rows at a time, such as: |
|
MSSQL |
Supported.(since version 2008) |
|
MySQL |
Supported. |
BOOLEAN Type⌘
|
Standard |
The BOOLEAN type is optional (has feature ID T031), which is a bit surprising for such a basic type. However, it seems that endless discussions of how NULL is to be interpreted for a boolean value is holding BOOLEAN from becoming a core type.The standard says that a BOOLEAN may be one of the following literals:
|
|
MSSQL |
Doesn't support the BOOLEAN type.Possible alternative type: the BIT type which may have 0 or 1 (or NULL) as value. If you insert an integer value other than these into a field of type BIT, then the inserted value will silently be converted to 1.Rudy Limeback has some notes about oddities with the MSSQL BIT type. |
|
MySQL |
Offers a non-conforming BOOLEAN type. MySQL's BOOLEAN is one of many aliases to its TINYINT(1) type.(Take care if you use TINYINT(1) and JDBC with MySQL and expect to get non-boolean values from it.)MySQL accepts the literals TRUE and FALSE as aliases to 1 and 0, respectively. However, you may also assign a value of � e.g. � 9 to a column of type BOOLEAN (which is non-conforming).If you use JDBC with MySQL, then BOOLEAN is the preferred type for booleans: MySQL's JDBC-driver implicitly converts between Java's boolean and MySQL's pseudo-BOOLEAN type.Side note: MySQL has a |
The CHAR type⌘
For the following section, I have used this test-SQL to try to illuminate differences (unfortunately, even standard SQL as simple as this has to be adjusted for some products): Test steps:
CREATE TABLE chartest (
charval1 CHAR(10) NOT NULL,
charval2 CHAR(10) NOT NULL,
varcharval VARCHAR(30) NOT NULL
);
INSERT INTO chartest VALUES ('aaa','aaa','aaa');
INSERT INTO chartest
VALUES ('aaaaaa ','aaa','aaa'); -- should truncate to 'aaaaaa '
INSERT INTO chartest
VALUES ('aaaaaaaaaaaa','aaa','aaa'); -- should raise error
SELECT * FROM chartest; -- should show two rows
DELETE FROM chartest WHERE charval1='aaaaaa';
SELECT * FROM chartest; -- should show one row
SELECT * FROM chartest WHERE charval1=varcharval;
SELECT charval1 || 'X' AS res FROM chartest;
SELECT CHAR_LENGTH(charval1 || charval2) AS res FROM chartest;
SELECT CHAR_LENGTH(charval1) + CHAR_LENGTH(charval2)
AS res
FROM chartest;
Expected results:
SELECT * FROM chartest; -- should show two rows CHARVAL1 CHARVAL2 VARCHARVAL ========== ========== ============================== aaa aaa aaa aaaaaa aaa aaa DELETE FROM chartest WHERE charval1='aaaaaa'; SELECT * FROM chartest; -- should show one row CHARVAL1 CHARVAL2 VARCHARVAL ========== ========== ============================== aaa aaa aaa SELECT * FROM chartest WHERE charval1=varcharval; CHARVAL1 CHARVAL2 VARCHARVAL ========== ========== ============================== aaa aaa aaa
SELECT charval1 || 'X' FROM chartest AS res; res =========== aaa X
SELECT CHAR_LENGTH(charval1 || charval2) AS res FROM chartest;
res
===========
20
SELECT character_length(charval1) + character_length(charval2)
AS res
FROM chartest;
res
============
20
Actual Results⌘
|
Standard |
|
|
MSSQL |
Generally follows standard, but (conceptually) truncates trailing white-space before performing some functions (at least before |
|
MySQL |
Breaks the standard by silently inserting the string, truncated to specified column CHAR-length. |
The TIMESTAMP type⌘
|
Standard |
Part of the Core requirements, feature ID F051-03.
|
|
MSSQL |
Note that MSSQL's choice of words related to date and time is confusing: In MSSQL's vocabulary, datetime is a concrete data type, whereas in the SQL standard, datetime is a general term covering the DATE, TIME and TIMESTAMP types.MSSQL has a strange pseudo-type called TIMESTAMP, but has deprecated it; don't use it in new code.The closest match to the SQL standard's TIMESTAMP type is DATETIME. This type stores the combination of date and time. It has a maximum of three fractional digits for seconds.Performs good sanity checks on inserted timestamp values; e.g. this will work: |
|
MySQL |
No matter what date/time data type chosen in MySQL, storage of fractional seconds and time zones are not supported (the |
SQL Functions⌘
Character Length
|
Standard |
|
|
MSSQL |
Doesn't have CHARACTER_LENGTH. Provides the |
|
MySQL |
Provides CHARACTER_LENGTH. |
SUBSTRING⌘
|
Standard |
The standard defines two variants of the SUBSTRING function:1. To comply with Core SQL (Feature E021-06), the DBMS must support an 'ordinary' SUBSTRING function which extracts characters from a string: |
|
MSSQL |
MSSQL has a |
|
MySQL |
MySQL supports the standard's ordinary SUBSTRING function, with some twists (see below). No regular expression based substring extraction is supported.
|
REPLACE⌘
|
Standard |
Not mentioned. May be obtained through a combination of other functions (have a look at the OVERLAY, POSITION and CHARACTER_LENGTH functions). |
|
MSSQL |
Follows de facto standard with the exception that MSSQL by default works case insensitively. |
|
MySQL |
Follows de facto standard. |
TRIM⌘
|
Standard |
Core SQL feature ID E021-09: |
|
MSSQL |
Doesn't support the standard TRIM function.Provides |
|
MySQL |
Follows the standard. |
LOCALTIMESTAMP⌘
It's often important to get the value of current date and time. Below are the functions used to do that in the different implementations.
|
Standard |
The current timestamp (without time zone) is retrieved with the LOCALTIMESTAMP function which may be used as: |
|
MSSQL |
Doesn't have the LOCALTIMESTAMP function.Instead, it has CURRENT_TIMESTAMP which�however�doesn't return a value of TIMESTAMP WITH TIME ZONE, but rather a value of MSSQL's DATETIME type (which doesn't contain time zone information). |
|
MySQL |
Follows the standard. |
Concatenation⌘
|
Standard |
Core feature ID E021-07: |
|
MSSQL |
Breaks the standard by using the '+' operator instead of '||'.Does not automatically cast operands to compatible types. If an operand is NULL, then the result is NULL. |
|
MySQL |
Badly breaks the standard by redefining |
Constraint handling⌘
The UNIQUE constraint
|
Standard |
As the constraint name indicates, a (set of) column(s) with a UNIQUE constraint may only contain unique (combinations of) values.A column�or a set of columns�which is subject to a UNIQUE constraint must also be subject to a not NULL constraint, unless the DBMS implements an optional "NULLs allowed" feature (Feature ID 591). The optional feature adds some additional characteristics to the UNIQUE constraint:1. Columns involved in a UNIQUE constraint may also have NOT NULL constraints, but they do not have to.2. If columns with UNIQUE constraints do not also have NOT NULL constraints, then the columns may contain any number of NULL-'values'. (Logical consequence of the fact that NULL<>NULL.) |
|
MSSQL |
Follows the standard�with a twist:MSSQL offers the NULLs allowed feature, but allows at most one instance of a NULL-'value', if NULLs are allowed; i.e. breaks characteristic 2 in the above description of the standard. |
|
MySQL |
Follows the standard, including the optional NULLs allowed feature. |
Automatic key generation⌘
It's sometimes handy to have the platform handle generation of keys. The platforms offer various means for this.
|
Standard |
The standard specifies a column attribute of:
|
|
MSSQL |
MSSQL offers IDENTITY as a column property, but with a different syntax than the standard's specification. An example of creating a table with an IDENTITY column: |
|
MySQL |
MySQL doesn't support the standard's IDENTITY attribute.As an alternative, an integer column may be assigned the non-standard |
TRUNCATE TABLE⌘
It's sometimes useful to be able to remove all rows from a large table in a quick way. And often, DELETE isn't as quick as we want. So several DBMSes implement a TRUNCATE operation. Typically, truncating means that deletion isn't associated with triggers which may exist for the table, and typically, truncating involves little (if any) transaction log activity.
|
Standard |
The SQL standard defines the |
|
MSSQL |
Follows the standard.In MSSQL, |
|
MySQL |
MySQL has a |
Command line procedures / metadata⌘
The following are not necessarily SQL operations, but rather a description of how different operations are performed in the command line interface provided by each product.
- some people hate using CLI
- some people can't imagine not using it for everything
Starting the command line interface⌘
|
Standard |
Not defined. |
|
MSSQL |
The command line interface is started by running |
|
MySQL |
Run: |
Databases vs. Schemas⌘
The SQL specification makes clear what an "SQL schema" is; however, different databases implement it incorrectly. To compound this confusion the functionality can, when incorrectly implemented, overlap with that of the parent-database. An SQL schema is simply a namespace within a database, things within this namespace are addressed using the member operator dot ".". This seems to be a universal amongst all of the implementations.
Who cares?⌘
- example problem: former MySQL users may create multiple databases for one project. In this context, MySQL databases are analogous in function to Postgres-schemas, insomuch as Postgres lacks off-the-shelf cross-database functionality that MySQL has. Conversely, PostgreSQL has applied more of the specification implementing cross-table, cross-schema, and then left room for future cross-database functionality.
- MySQL aliases schema with database behind the scenes, such that CREATE SCHEMA and CREATE DATABASE are analogs. It can therefore be said that MySQL has implemented cross-database functionality, skipped schema functionality entirely, and provided similar functionality into their implementation of a database. In summary, Postgres fully supports schemas but lacks some functionality MySQL has with databases, while MySQL does not even attempt to support true schemas
Getting a list of databases⌘
|
Standard |
Not specified. (FYI: The SQL standard doesn't have the concept of adatabase as a container of schemas; instead, the standard specifies that schemas are contained in a catalog.) |
|
MSSQL |
|
|
MySQL |
|
Getting a list of schemas⌘
|
Standard |
|
|
MSSQL |
Follows the standard. |
|
MySQL |
MySQL doesn't support schemas. (but there's a hack in the mysql DB) |
Getting a list of tables⌘
|
Standard |
Part 11 of the SQL standard specifies the INFORMATION_SCHEMA schema which must be part of all database catalogues. The schema may be used like this: |
|
MSSQL |
Follows that standard. |
|
MySQL |
Follows the standard, except that MySQL doesn't support schemas, so one might say that MySQL's |
Getting a table description⌘
|
Standard |
Part 11 of the SQL standard specifies the INFORMATION_SCHEMA schema which must be part of all database catalogues. The schema may be used like this: |
|
MSSQL |
Follows the standard, except that
|
|
MySQL |
Follows the standard, except that
|
Of course, there's always
describeshow create
Getting a query explanation⌘
|
Standard |
Not standardized. |
|
MSSQL |
MSSQL can be put in a query explanation mode where queries are not actually executed, but a query explanation is returned instead: |
|
MySQL |
|
Turning on query timing⌘
|
Standard |
Not standardized. |
|
MSSQL |
|
|
MySQL |
MySQL's command line interface prints query times by default. |
JDBC⌘
|
MSSQL |
Microsoft's driver: sqljdbc.jar - read more |
|
MySQL |
The MySQL Connector/J driver: mysql-connector-java-[version]-bin.jar |
Dummy table⌘
Some DBMSes let you perform a query like this:
SELECT 1+1
answering
2
With other DBMSes, you need to insert a dummy-table expression to obtain the same result:
SELECT 1+1 FROM dummy-table
|
MSSQL |
No need for dummy-table. |
|
MySQL |
No need for dummy-table, although MySQL allows you to refer to a |
Getting Versions⌘
|
Standard |
|
|
MSSQL |
MSSQL's implementation of the IMPLEMENTATION_SCHEMA doesn't seem to include the SQL_IMPLEMENTATION_INFO view. In stead, you may use |
|
MySQL |
MySQL's |